Introduction to J2EE (2.x), its Architecture and Component Diagram
October 9, 2012 Leave a comment
Java 2 Platform enterprise edition is an integrated set of individual APIs required for developing server side MULTI-TYRED, DISTRIBUTED, TRANSACTIONAL and SECURE applications.
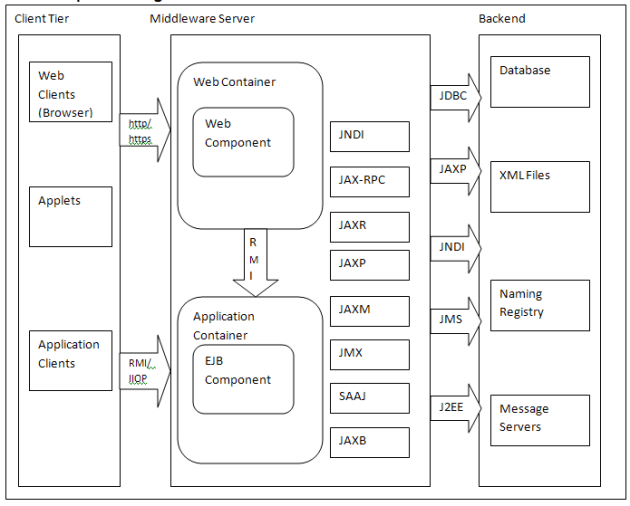
J2EE Component Diagram
J2EE is released in 4 parts:
• J2EE Specification: which declares all the APIs included in the release
• J2EE Reference Implementation: Open source implementation for the APIs given under J2EE spec and is provided by SUN i.e, j2sdkee
This is given to prove that APIs given under the spec are properly implemented
To help 3rd party vendors (as a reference) to implement the spec
• J2EE Test Suit: It provides compatibility test suit which can be used to confirm the J2EE product.
• J2EE Blue Print: This includes some best practices of the J2EE APIs provided
J2EE Architecture
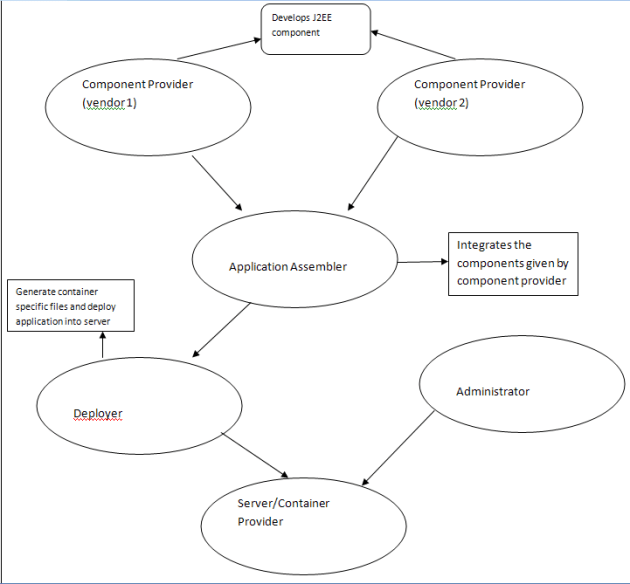
Components:
• Component Provider: It is responsible for implementing components i.e, responsible to implement core business logic. Here the provider is required to be strong in programming, component architectures, component life cycles and with good business domain knowledge. The outcome from this provider will be JAR files containing components
• Application Assembler: It will take the components developed by the component provider and assemble them into an application. Here he may be required to write some simple client components. It uses J2EE standards to integrate components like some parts of deployment descriptors and some configuration files.
• Container provider: is responsible to implement low level services which are required to run the component like security, transactions, life cycle management etc..
• Server provider: responsible to provide system level services. Server and container providers must be same
• Deployer: is responsible to take the application assembled by the assembler and configure it so that it can be placed on top of a server/container. He is required to write vendor specific deployment descriptors and configuration files.
• Administrators: is responsible to configure the resources required for the application in the server, like creating users, configuring connection pools, etc..
Recent Comments